
How XDR Can Enable Enterprise-Wide Security
Now a days cyber-crimes are at their peak; therefore, businesses need more than just the usual […]

AWS launches tools to tackle evolving cloud security threats
The increasing sophistication and scale of cyber threats pose a growing challenge for enterprises managing complex […]

Working in critical infrastructure? Boost your effectiveness with these cybersecurity certifications
Hybrid warfare between nation-states is imperilling critical infrastructure around the world, both physically and electronically. Since […]
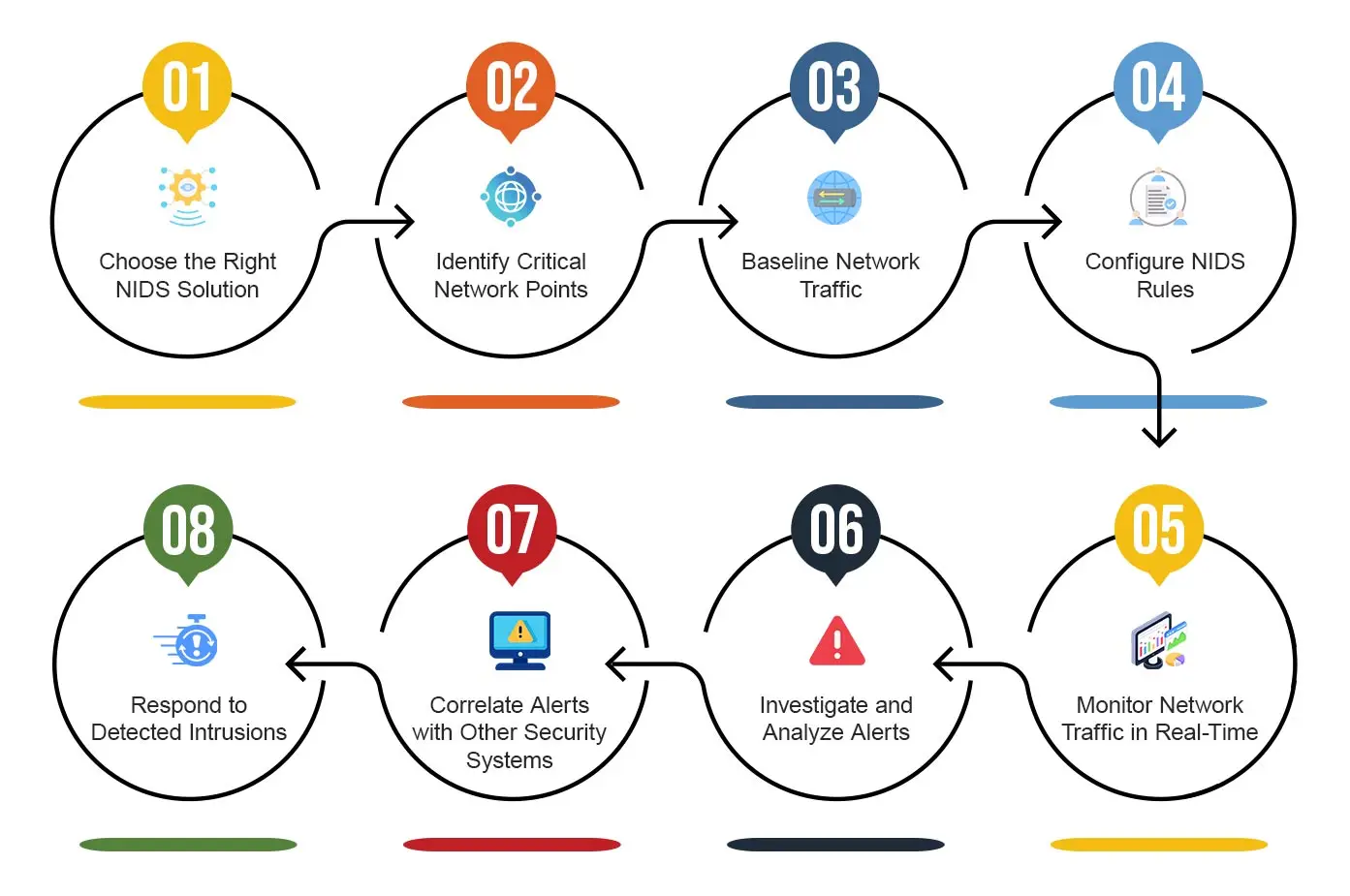
Building a Resilient Network Defense with Network Based Intrusion Detection Systems
Network based Intrusion Detection System (NIDS) is an important layer of security in the cybersecurity world. […]

Popular game script spoofed to infect thousands of game developers
A malware loader, now named GodLoader, has been observed to be using Godot, a free and […]

Ransomware-Trend: Hacker mit Zerstörungsdrang
Hacker setzen bei Ransomware-Angriffen immer häufiger auf Zerstörung und nicht mehr “nur” auf Erpressung. Gearstd – […]

Security-FinOps collaboration can reap hidden cloud benefits: 11 tips
For enterprises operating on the cloud, security and cost management are rising concerns. Typically, these issues […]

Cloudflare-Vorfall führt zu massivem Verlust an Logs
Unzureichend getestete Systeme und falsch konfigurierte Schutzmechanismen haben zu einem massiven Datenverlust geführt. T. Schneider/shutterstock.com Am […]

Instagram-Seite der CSU im Bundestag gehackt
de-nue-pic – Shutterstock.com Die Instragram-Seite der CSU-Landesgruppe im Bundestag ist gehackt worden – es wurden kurzzeitig Pro-Palästinensische Inhalte gepostet. Das […]

Die gefährlichsten Software-Schwachstellen 2024
MITRE hat die 25 häufigsten und schwerwiegendsten Software-Schwachstellen des Jahres 2024 ermittelt. solarseven/shutterstock.com Die US-Cybersicherheitsbehörde CISA […]
