
After fake employees, fake enterprises are next hiring threat to corporate data
Chinese companies are trying to cut Taiwan’s lead in semiconductor technology by hiring away its best […]

Infostealer malware poses potent threat despite recent takedowns
Despite the takedown of Redline — the most prolific stealer of 2024 — and Meta Stealer […]

6 hard-earned tips for leading through a cyberattack — from CSOs who’ve been there
An incident response plan is central to ensuring your organization is prepared for a cyberattack. But […]
7 Wege, Daten (besser) zu verschlüsseln
Verschlüsseln Sie Ihre Daten zeitgemäß? JLStock | shutterstock.com Das Konzept der Kryptografie existiert schon ein paar […]

Volume of attacks on network devices shows need to replace end of life devices quickly
Two of the top three vulnerabilities that threat actors tried to leverage in 2024 were in […]

Hackerangriff auf MAN-Tochter
Cyberkriminelle haben offenbar die Systeme einer MAN-Tochter geknackt. Die Zentrale in München ist nach eigenen Angaben […]

Hacker wollten Arbeitslosengeld ergaunern
width=”1936″ height=”1089″ sizes=”(max-width: 1936px) 100vw, 1936px”>Die Bundesagentur hat Strafanzeige gestellt. Bundesagentur für Arbeit Bei der Bundesagentur […]

How CISOs can balance business continuity with other responsibilities
Cyber incidents, especially ransomware, are changing the way businesses assess risk and resiliency. As a result, […]

Authentifizierungslösungen: 10 Passwordless-Optionen für Unternehmen
Um Passwörter hinter sich zu lassen, gibt es bessere Lösungen. Wir zeigen Ihnen zehn. Foto: Raffi […]
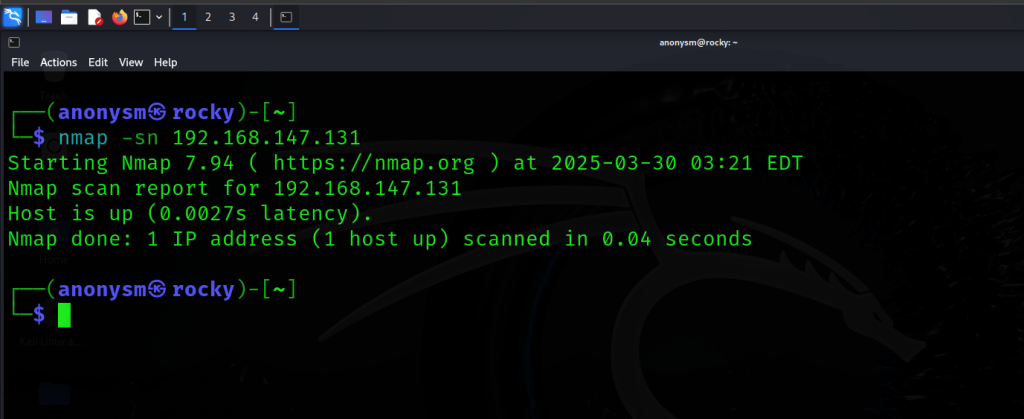
The Ultimate Nmap Guide: Master Network Scanning, Scripting, and Security Audits
Hey guys, Rocky here! Welcome to your ultimate guide to Nmap—the Swiss Army knife of networking […]
