
Threat Hunting: Strategic Approaches and Capabilities to Uncover Hidden Threats
What is Threat Hunting? Threat hunting is the discovery of malicious artifacts, activity or detection methods […]
Understanding the Importance of XDR
Cyber threats hide everywhere, and the numbers are shocking—more than 80% of companies dealt with a […]
5 Reasons You Should Consider Relooking Your DLP Strategy
Companies across industries have invested a lot of money in Data Loss Prevention (DLP) solutions, thinking […]
eWeek TweetChat, November 19, Cybersecurity and AI: Challenges and Solutions
Join eWeek at 2 PM Eastern/11 AM Pacific on Tuesday, November 19, for a lively, in-depth […]

The Ultimate Guide to Bathroom Renovation: Planning, Design, and Execution
Bathroom renovations can transform one of the most important spaces in your home into a more […]
What to look for in Cloud Security
Cloud computing is changing how companies handle their data, providing unparalleled scalability and flexibility. Gartner predicts […]

How to Manage Money for Retired Individuals: A Comprehensive Guide
Retirement is a pivotal life stage that brings with it new financial challenges and opportunities. After […]

Comprehensive Guide to Home Care Services: Everything You Need to Know
Introduction In an aging world, home care services have become an essential component of healthcare systems. […]
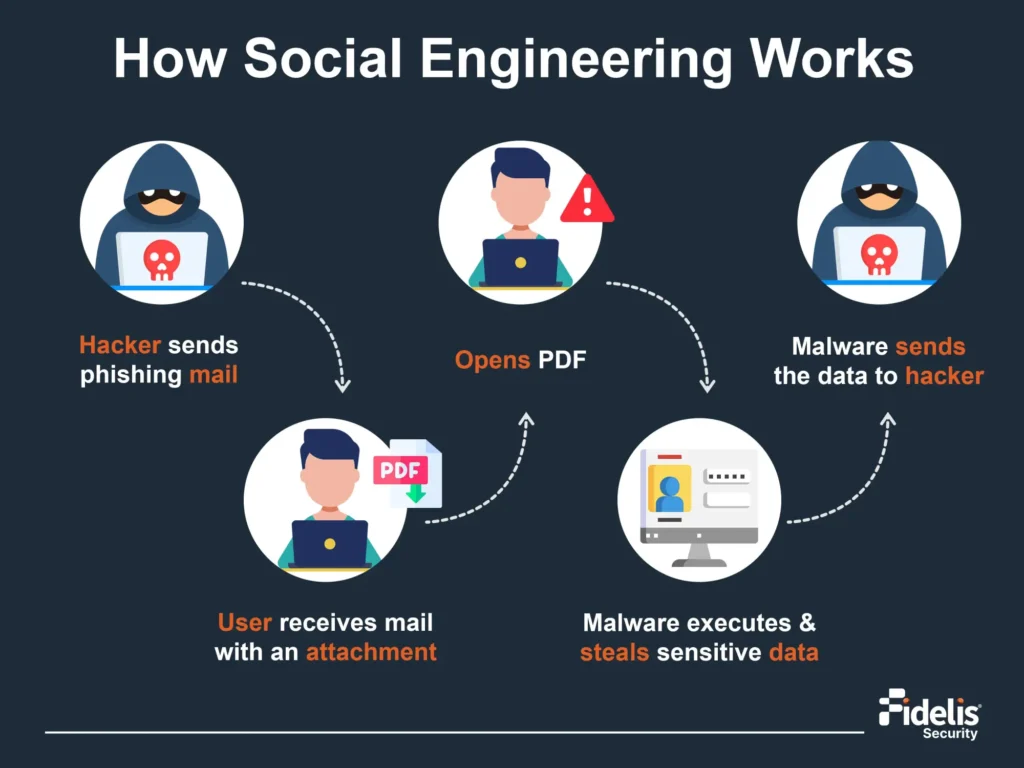
Leading Reason for Data Loss: Social Engineering & Insider Threats
When it comes to data loss, the biggest yet common dangers these days come from within […]
What is a cyberattack?
What is a cyberattack? Cyberattacks aim to damage or gain control or access to important documents […]
