
Is your perimeter having an identity crisis?
For years, you’ve operated on a fundamental and fragile assumption that with enough training and the […]

Step-by-Step Guide to CNAPP Implementation: Securing Cloud-Native Applications
Key Takeaways CNAPP closes the security gaps traditional tools miss in dynamic cloud environments. It protects […]

Top 7 agentic AI use cases for cybersecurity
Agentic AI promises to revolutionize a wide range of IT operations and services, including cybersecurity. While […]
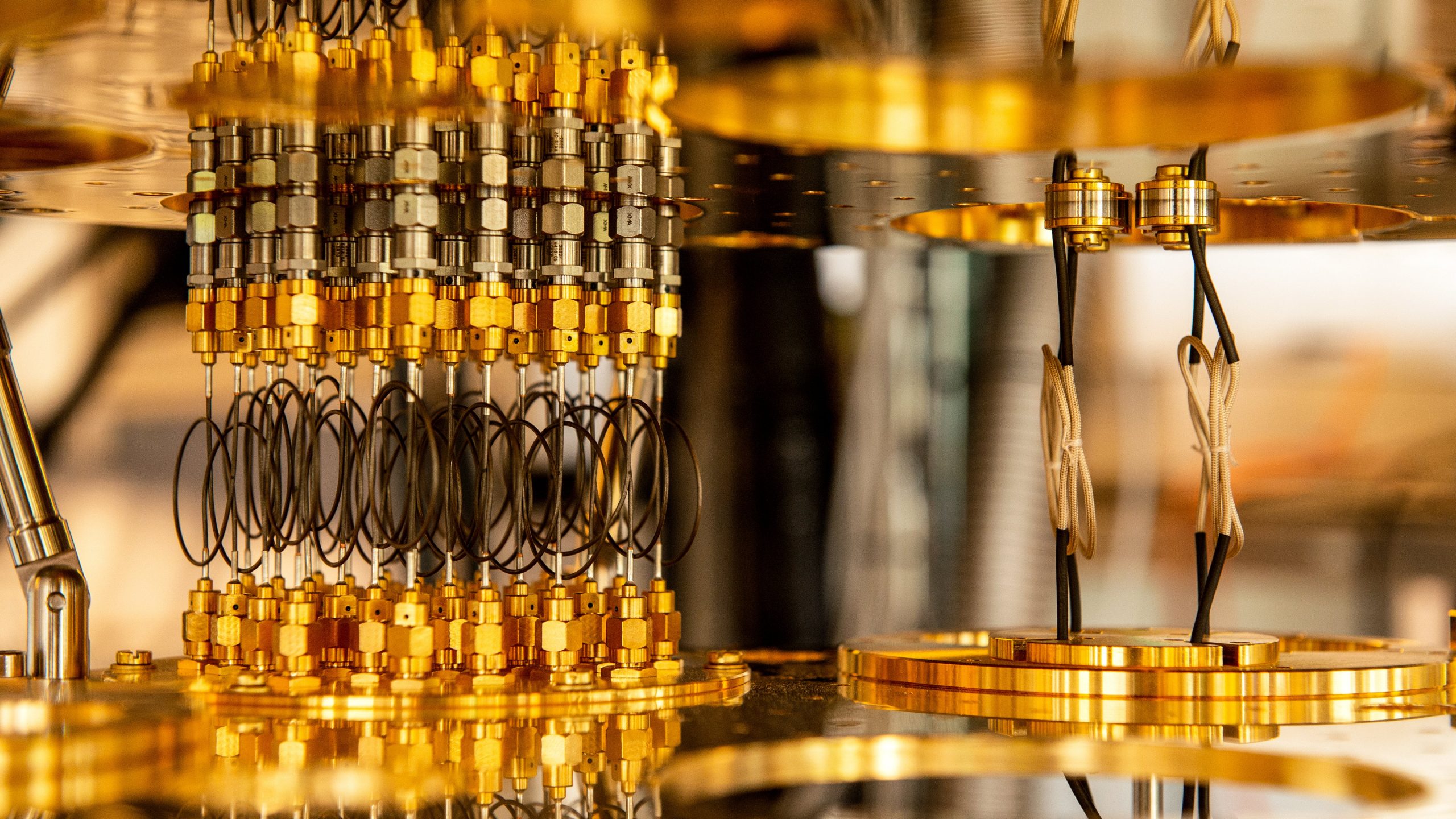
Notable post-quantum cryptography initiatives paving the way toward Q-Day
The point at which quantum computers will be capable of breaking existing cryptographic algorithms — known […]

Software Bill of Material umsetzen: Die besten SBOM-Tools
Nur wenn Sie wissen, was drinsteckt, können Sie sich sicher sein, dass alles mit rechten Dingen […]

Atroposia malware kit lowers the bar for cybercrime — and raises the stakes for enterprise defenders
Cybercrime is increasingly being commoditized, significantly lowering the bar for hackers and making things tougher for […]

How evolving regulations are redefining CISO responsibility
CISOs face increasing personal and criminal liability for improper or incomplete risk management and disclosure during […]

Copilot diagrams could leak corporate emails via indirect prompt injection
Microsoft has patched an indirect prompt injection flaw in Microsoft 365 Copilot that could have allowed […]

Atlas browser exploit lets attackers hijack ChatGPT memory
Days after cybersecurity analysts warned enterprises against installing OpenAI’s new Atlas browser, researchers have discovered a […]

Volvo’s recent security breach: 5 tips to speed incident response while preserving forensic integrity
In August 2025, Volvo Group North America disclosed that it had been impacted by a data […]
