
Wie Model Context Protocol gehackt wird
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?quality=50&strip=all 4262w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/07/Victor-Moussa-shutterstock_1708840009_16z9.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
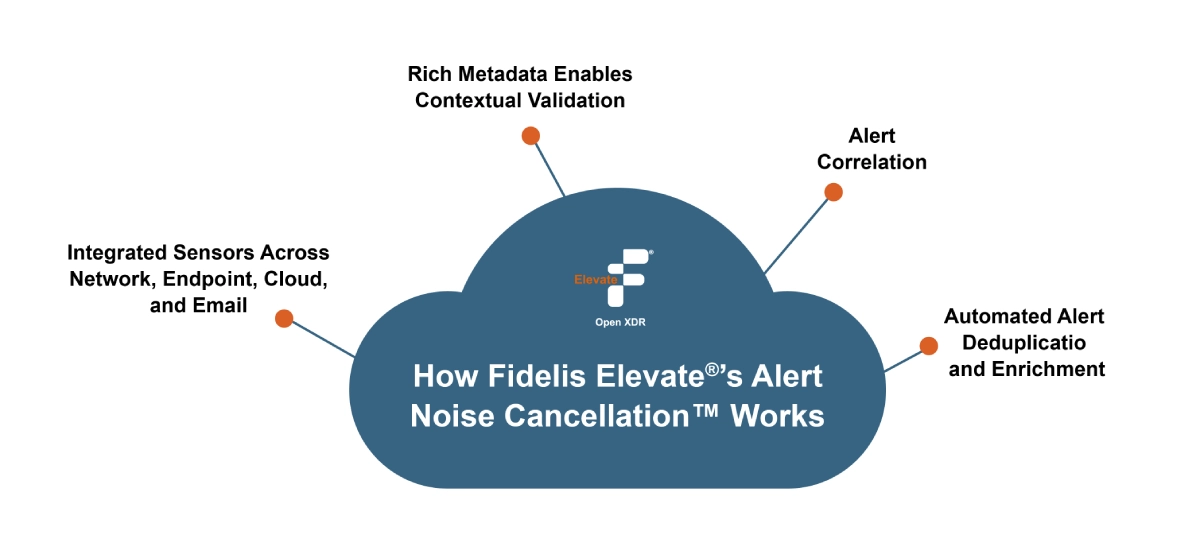
Alert Noise Cancellation™ Capability of Fidelis Elevate®: Understanding the Need
Today’s Security Operations Centers (SOCs) have plenty of data but are overwhelmed. A single attacker can […]

CISA bringt Open-Source-Plattform für digitale Forensik
Mit Thorium steht Unternehmen nun auch eine Open-Source-Plattform offen, um Malware zu analysieren. Gorodenkoff – shutterstock.com […]

Nvidia patches critical Triton server bugs that threaten AI model security
A surprising attack chain in Nvidia’s Triton Inference Server, starting with a seemingly minor memory-name leak, […]

TSMC-Mitarbeiter unter Spionageverdacht festgenommen
TSMC ist ein attraktives Ziel für Spionage. Vidpen | shutterstock.com Drei Mitarbeiter des weltgrößten Auftragsfertigers für […]

The age of infostealers is here. Is your financial service secure?
In the sophisticated world of financial services, trust is more than a buzzword — it’s the […]
Why BFSI needs column-level encryption
The BFSI (Banking, Financial Services, and Insurance) industry is experiencing constant pressure on cybersecurity issues in […]

5 hard truths of a career in cybersecurity — and how to navigate them
Cybersecurity is an exceptionally promising career path. Demand for cyber talent is high, as is compensation, […]

The Link Between Asset Classification and Threat Response Accuracy
The cybersecurity landscape continues to evolve at an unprecedented pace, with organizations facing increasingly sophisticated threats […]

OAuth-Apps für M365-Phishing missbraucht
Gefälschte OAuth-Apps eröffnen Angreifern neue Wege, um Microsoft-Konten zu kapern. janews – Shutterstock.com Bedrohungsakteure haben einen […]
