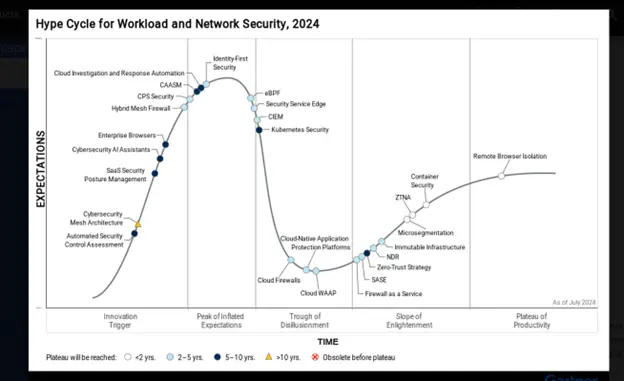
NDR in the Era of Cloud and Hybrid Environments: Why It’s Essential
“The PwC Cybersecurity Outlook Report reveals that 39% of UK senior executives expect cloud-related threats to […]

Möglicher Cyberangriff: IT-Ausfall bei Medion
Zunächst hat Medion einen Cyberangriff als Ursache für den IT-Ausfall genannt. Mittlerweile spricht das Unternehmen “nur” […]

SmokeLoader picks up ancient MS Office bugs to pack fresh credential stealer
Threat actors are using a well-known modular malware loader, SmokeLoader, to exploit known Microsoft Office vulnerabilities […]

EU enacts new laws to strengthen cybersecurity defenses and coordination
The European Union has enacted two new laws to bolster its cybersecurity defenses and coordination mechanisms. […]

10 most critical LLM vulnerabilities
Enterprise adoption of generative AI technologies has exploded in 2024 due to the rapid evolution of […]

Want to be a cybersecurity pro? Use generative AI to get some simulated training
I often get approached by young, ambitious people looking to start a cybersecurity career. Some are […]

Der Weg zum nachhaltigen Cyberschutz
Wenn im Ernstfall Unternehmen stillstehen, sind die Sorgen groß. Mit Cyberresilienz tragen CISOs dazu bei, dass […]

Why identity security is your best companion for uncharted compliance challenges
In today’s rapidly evolving global regulatory landscape, new technologies, environments, and threats are heightening cybersecurity and […]

Intelligent Privilege Controls™: A quick guide to secure every identity
Security used to be simpler. Employees, servers, and applications were on site. IT admins were the […]

CIO POV: Building trust in cyberspace
Trust lies at the heart of every relationship, transaction, and encounter. Yet in cyberspace—where we work, […]
