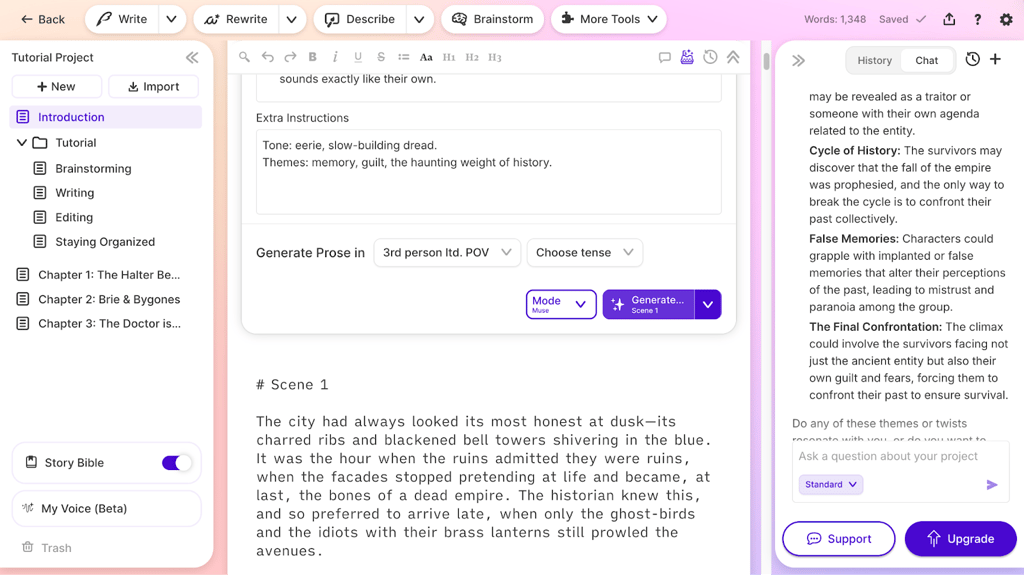
Best AI Tools for Fans of Horror Films
From haunted movie scripts to eerie visuals, AI tools are quietly making their mark on horror […]
Fans Cry ‘Hypocrisy’ as Taylor Swift Is Accused of Using AI for New Album Promo
It was supposed to be a fun treasure hunt for her fans. But a promotional campaign […]

58% of CISOs are boosting AI security budgets
AI is no longer an experiment in the security stack — it’s becoming the centerpiece. Foundry’s […]

Source code and vulnerability info stolen from F5 Networks
CSOs with equipment from F5 Networks in their environment should patch their devices immediately and be […]
AI Just Designed Viruses That Kill Bacteria… And They Actually Work
Stanford scientists just crossed a wild milestone: they used AI to design viruses from scratch that […]
Army Planning AI-Focused ‘Disruptive Technology’ Pilot to Expedite HR Processes
Say goodbye to military HR paperwork. The Army’s betting on AI to handle the heavy lifting. […]
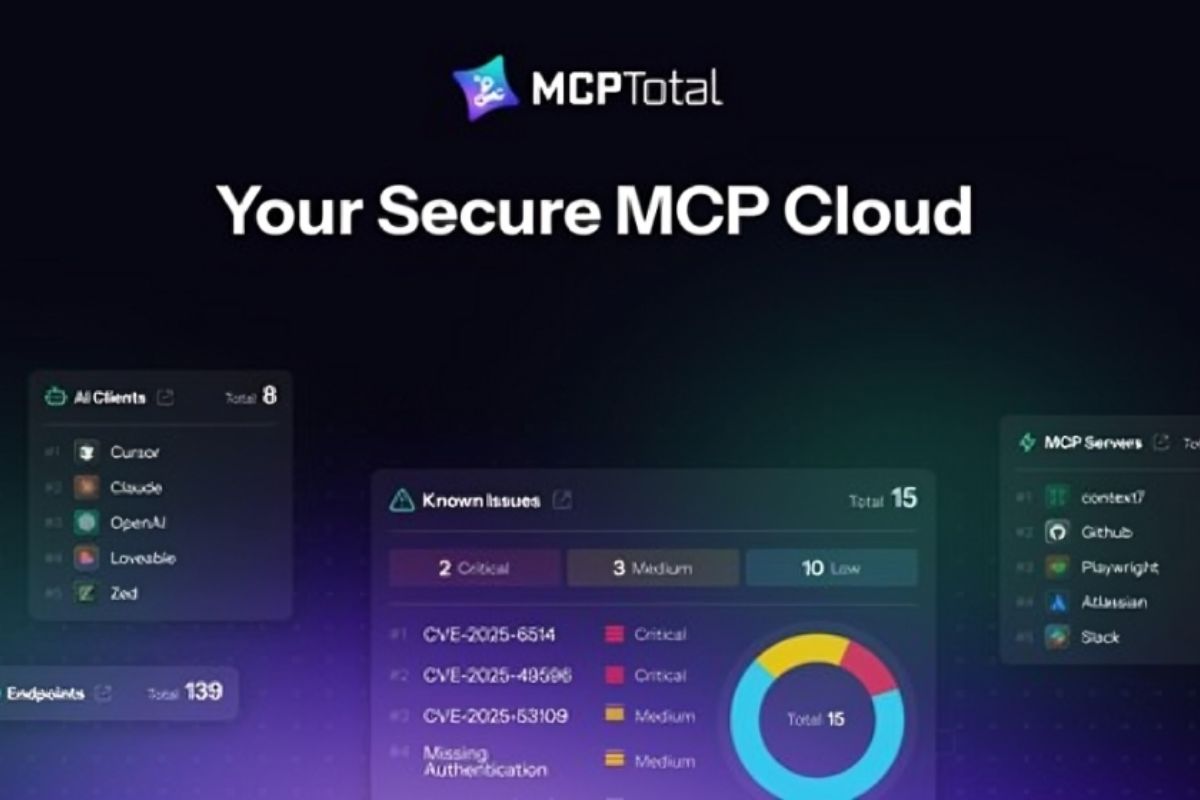
MCPTotal Launches to Power Secure Enterprise MCP Workflows
MCPTotal, a comprehensive secure Model Context Protocol (MCP) platform, today announced its flagship platform to help […]
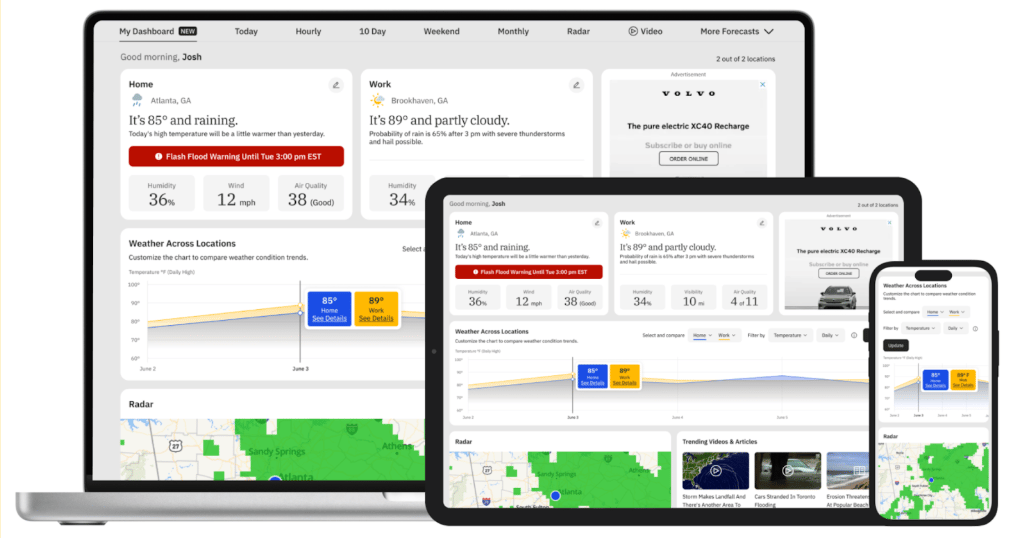
Best AI Tools for Weather Forecasts
For industries such as aviation, agriculture, and energy, weather forecasts aren’t trivial. They’re actually critical data […]
Walmart, OpenAI Partnership Turns ChatGPT Into Checkout Counter
The world’s largest retailer is betting big on generative AI, joining forces with OpenAI to turn […]
Humanity AI Pledges $500M to Put People at Center of AI Revolution
Artificial intelligence may be the technology of the decade, but a new $500 million initiative aims […]
