
Das CISO-Paradoxon: Innovation ermöglichen und Risiken managen
CISOs sollten eng mit anderen Teams zusammenarbeiten. eamesBot – shutterstock.com Eine der Hauptaufgaben von CISOs besteht […]

Coupang breach of 33.7 million accounts allegedly involved engineer insider
A prolonged lack of management of valid authentication keys for signed access tokens issued to authenticators […]

Suspicious traffic could be testing CDN evasion, says expert
An individual or group is doing new probing of content delivery networks (CDNs), an effort that […]

AI creates new security risks for OT networks, warns NSA
The security of operational technology (OT) in critical infrastructure has been a recurring theme for years, […]

Give Me 5 Minutes and I’ll Fix Your Bug Bounty Strategy (The 2026 Blueprint)
Let’s be real. You’re putting in the hours. You’ve got your tools set up, you’re scoping […]

From feeds to flows: Using a unified linkage model to operationalize threat intelligence
The problem: Static intelligence in a dynamic world Every CISO knows the fatigue that comes with […]

Windows shortcuts’ use as a vector for malware may be cut short
A longstanding problem with the way Windows handles LNK shortcut files, which attackers have been abusing […]

Momberger: Betrug-E-Mails an Kunden im Umlauf
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?quality=50&strip=all 5150w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/12/shutterstock_2617671109.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
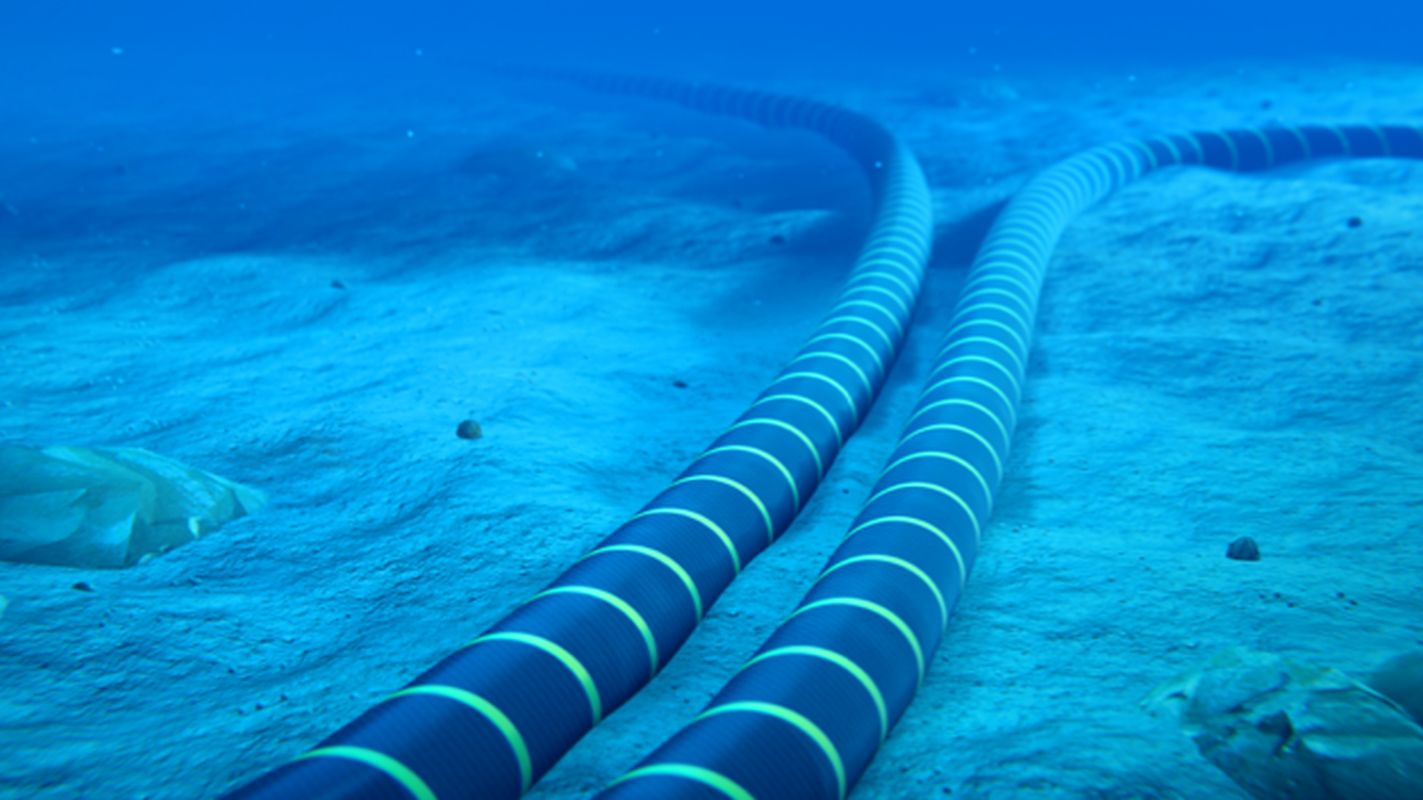
Submarine cable cybersecurity: protecting critical infrastructure
Between 95 and 99% of the world’s data traffic travels through submarine cables. An extensive network […]

Coach or mentor: What you need depends on where you are as a cyber leader
Renee Guttmann, a Fortune 50 CISO who has served at Time Warner, Coca-Cola, Royal Caribbean Cruises, […]
