Safeguarding Your Digital Assets: The Crucial Role of Enterprise Key Management Systems
In today’s digital age, the landscape of cybersecurity is complex and ever evolving. Protecting sensitive information […]
Mobile SDK Security: Effective Testing Methodology
In mobile penetration testing, third-party modules or libraries are often considered out of scope for several […]
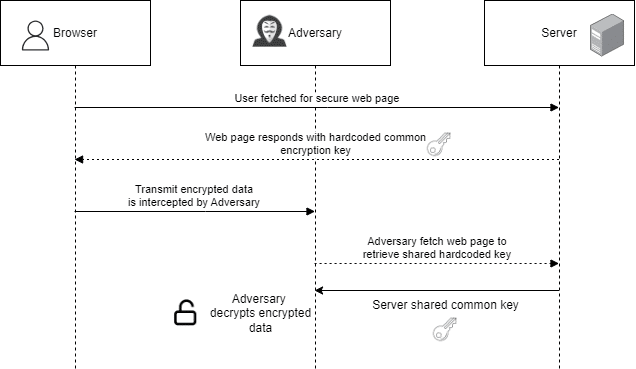
How Poor Cryptographic Practices Endanger Banking Software Security
In today’s digital age, financial institutions rely heavily on encryption to protect sensitive data in their […]
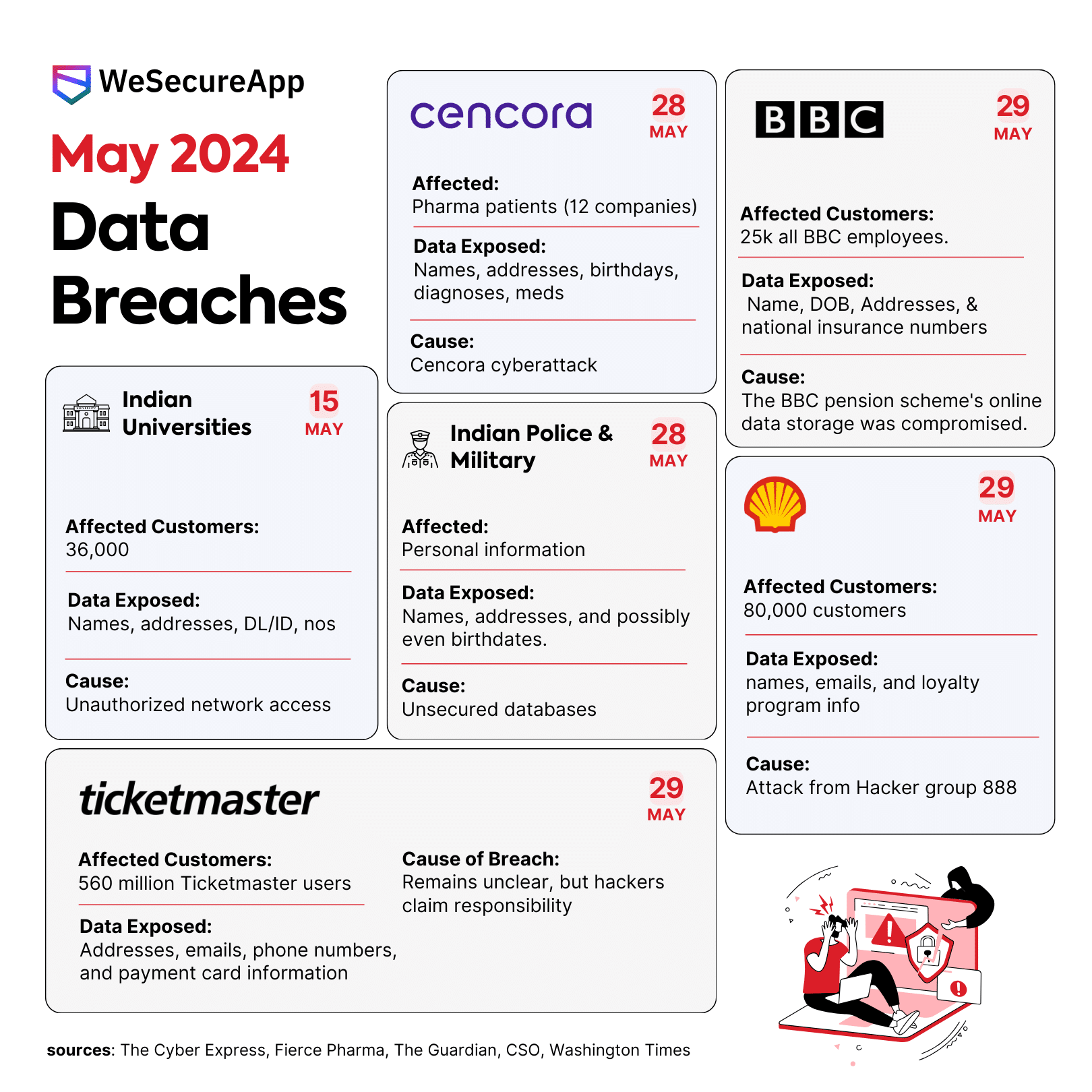
Data Breaches in May 2024 – Infographic
Has your data ever felt…exposed? We’ve all heard about data breaches, but have you ever stopped […]
Forescout CEO Barry Mainz on Operational Technology and Cybersecurity
I spoke with Barry Mainz, CEO of Forescout, about the key trends impacting security in operational […]
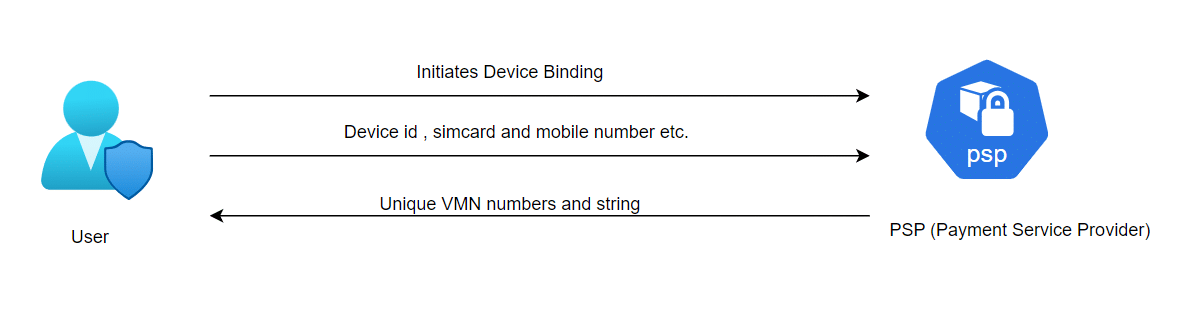
Device Binding to Protect Your Banking and UPI Apps
In an era where cyber threats are becoming increasingly sophisticated, securing sensitive data has never been […]
GCP Penetration Testing | Google Cloud Platform Security
Cloud Platforms are being adopted at an increasingly rapid pace. Cloud platforms like Google Cloud Platform […]
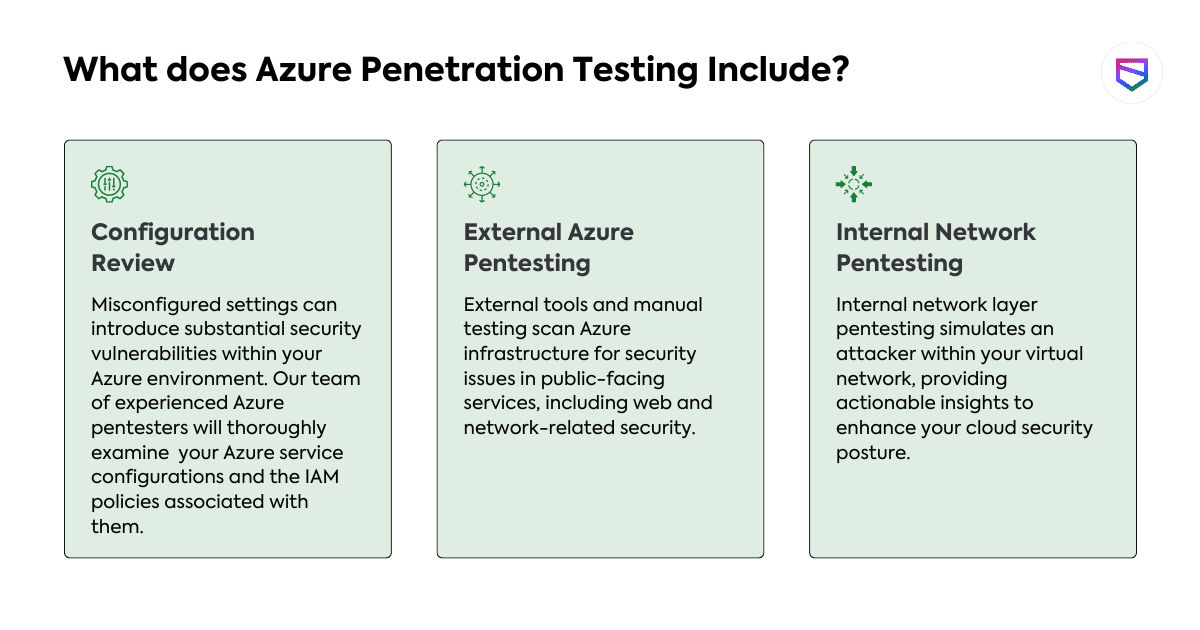
Azure Penetration Testing – Cloud Security Audits | Microsoft
Did you know? As per Microsoft, more than 95 percent of Fortune 500 companies use Azure. […]
End-2-End and server to server encryption over home network
#NAME? The post End-2-End and server to server encryption over home network appeared first on Blog […]
As a company how can we prevent penetration testers from compromising our system?
#NAME? The post As a company how can we prevent penetration testers from compromising our system? […]
